DNS Records
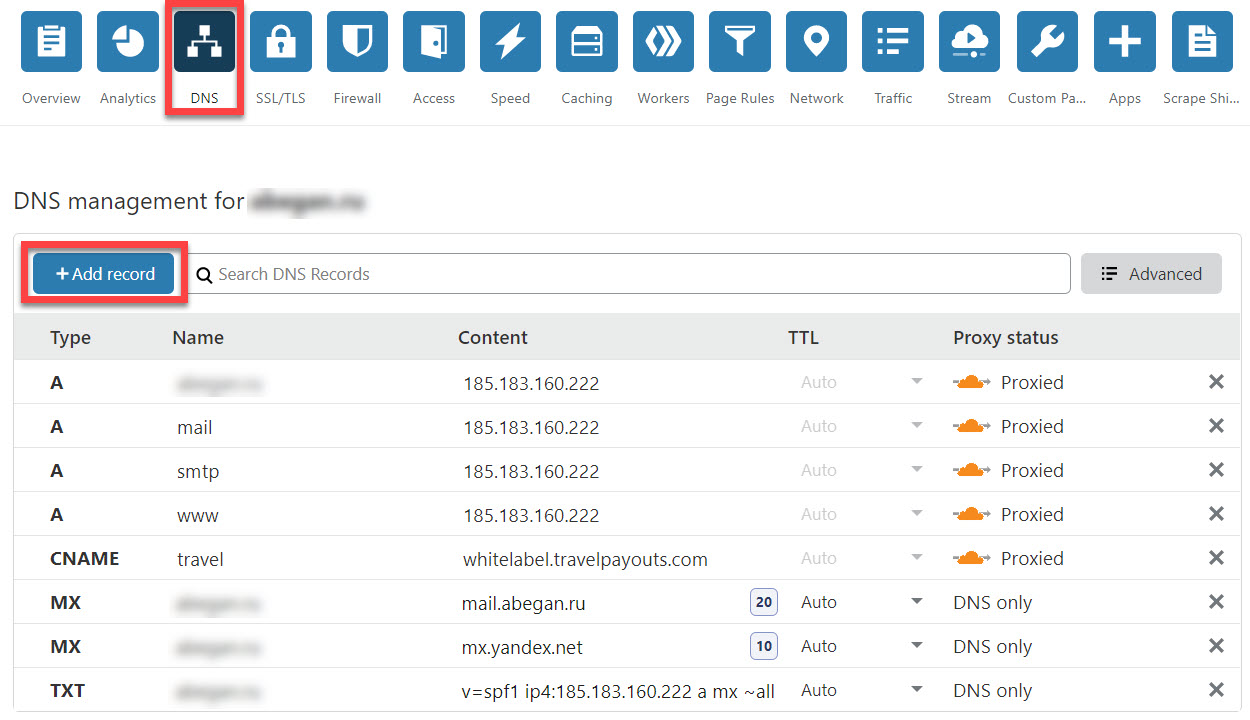
What is DNS and Why is DNS Needed? DNS stands for ‘Domain Name System’ or ‘Domain Name Server.’ All web sites, web apps and other resources on the internet are uniquely identified through IP addresses. For example, 8.8.8.8 is google.com’s IP address. Computers work well with numbers, but humans cannot remember the IP addresses of all the resources that they want to visit on the internet and words are easier to remember than a string of numbers (in case of IPv4) or an alphanumeric string (in case of IPv6), so every resource has a unique URL (Eg: github.com) that makes it easy to remember the name to get to the intended resource. Now resources can only be contacted by knowing their IP addresses, so there has to be some mapping for domain names to their IP addresses. Here is where the Domain Name System Protocol steps in, wherein the device from which a request is made for a resource first hits a Domain Name Server to get the IP address of the requested resource and uses that IP address to then contact the requested resource to fetch it. The DNS protocol is an Application Layer protocol that uses port 53 and mainly uses UDP as its Transport Layer protocol. Common DNS Records DNS records are used to provide important information about a domain. They are also called ‘Resource Records’ (RRs) and are stored in DNS Zone Files, which are stored on the domain’s Name Server. Almost every record follows the format Name TTL Class Type Data. Eg: www 86400 IN A 192.168.1.1 Name/Host The host name of the record. Also called ‘hostname.’ Eg values: @ (blank), a subdomain (www, blog, links, etc.), * (wildcard), etc. Eg usage If the host value is www for the domain harshkapadia.me, then the record is pertaining to www.harshkapadia.me. Similarly, if the host value is @ (blank) for the domain harshkapadia.me, then the record is pertaining to harshkapadia.me, ie, the base domain itself, so the output will have @ replaced by harshkapadia.me.. TTL Time To Live in seconds, unless otherwise mentioned. Lists the time for which DNS servers should cache the record. An update to the record will thus take time to reflect, as the previous value might be cached. Class It defines the protocol family. IN stands for ‘Internet’ and is used the most. More on classes Type Type of DNS record. There are more than 260 RR types defined by IANA! The most common ones are discussed below. Eg: A record, CNAME record, etc. Data/Value An IP address to which the record points or any other data that should be contained in the record. NOTE: For the following record sections, the base/apex/root domain is harshkapadia.me. ...